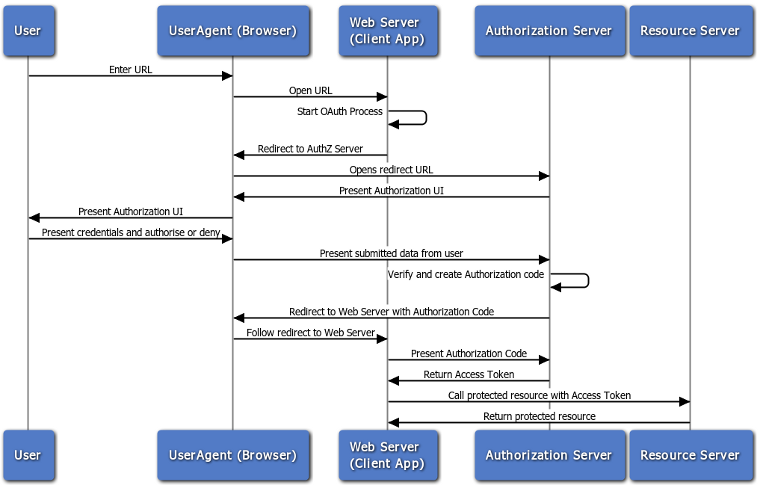
First we have to setup our JDeveloper (11.1.2.3.0) for the ADF mobile development.
1.Entry:That is the adfmf-feature.xml file.
This file is to configure the features of your application.
The adfmf-feature.xml file enables you to configure the actual mobile application features that are referenced by the element in the corresponding adfmf-application.xml file.So basically, what is says is, that adfmf-feature.xml is the configuration file of all the features your application might have.
All those features are stored in the adfmf-application.xml file.
That file is located in the descriptors section in JDeveloper.
2.What is that DataControl about?
That dataControl handles the operations on your device
Once we understand how it works. one step at a time. it is fairly easy to remember.
This is the beginning!
1.Entry:That is the adfmf-feature.xml file.
This file is to configure the features of your application.
The adfmf-feature.xml file enables you to configure the actual mobile application features that are referenced by the element in the corresponding adfmf-application.xml file.So basically, what is says is, that adfmf-feature.xml is the configuration file of all the features your application might have.
All those features are stored in the adfmf-application.xml file.
That file is located in the descriptors section in JDeveloper.
2.What is that DataControl about?
That dataControl handles the operations on your device
Once we understand how it works. one step at a time. it is fairly easy to remember.
This is the beginning!