Overview
The API Gateway can use the OAuth 2.0 protocol for authentication and authorization.
The API Gateway can act as an OAuth 2.0 Authorization Server and supports several OAuth
2.0 flows that cover common Web server, JavaScript, device, installed application, and
server-to-server scenarios.
Authorization Code (or Web Server) Flow
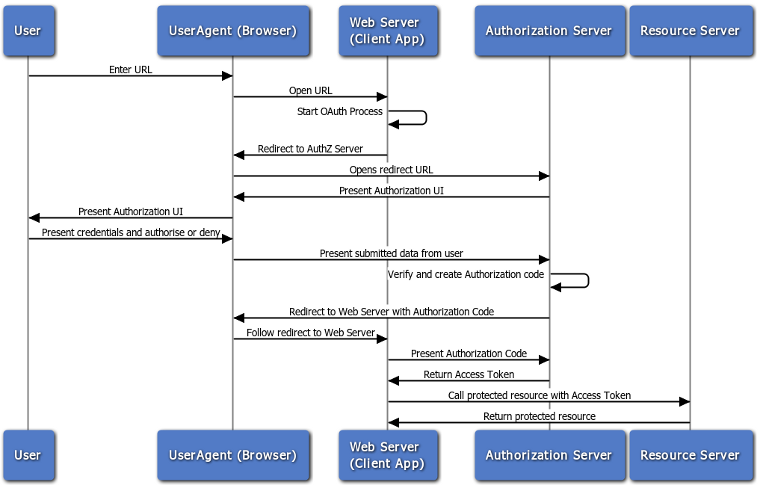
Obtaining an Access Token
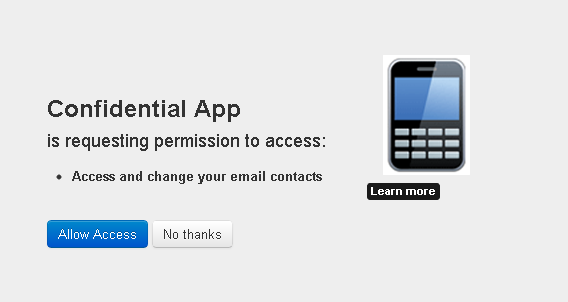
1. Redirect the user to the authorization endpoint with the following parameters:
| Parameter | Description |
response_type |
Required. Must be set to code.
|
client_id |
Required. The Client ID generated when the application was registered in the Oracle API Manager. |
redirect_uri |
Optional. Where the authorization code will be sent. This value must match one of the values provided in the Oracle API Manager. |
scope |
Optional. A space delimited list of scopes, which indicate the access to the Resource Owner's data being requested by the application. |
state |
Optional. Any state the consumer wants reflected back to it after approval during the callback. |
The following is an example URL:
https://apigateway/oauth/authorize?client_id=SampleConfidentialApp&
response_type=code&&redirect_uri=http%3A%2F%2Flocalhost%3A8090%2Fauth%2Fredirect.
html&scope=https%3A%2F%2Flocalhost%3A8090%2Fauth%2Fuserinfo.email
2. The response to the above request is sent to the
redirect_uri. For example:
https://localhost/oauth_callback&code=9srN6sqmjrvG5bWvNB42PCGju0TFVV
3. After the Web server receives the authorization code, it may exchange the authorization
code for an access token and a refresh token. This request is an HTTPS POST,
and includes the following parameters:
| Parameter | Description |
grant_type |
Required. Must be set to authorization_code.
|
code |
Required. The authorization code received in the redirect above. |
redirect_uri |
Required. The redirect URL registered for the application during application registration. |
client_id* |
Optional. The client_id obtained during application
registration.
|
client_secret* |
Optional. The client_secret obtained during
application registration.
|
format |
Optional. Expected return format. The default is
json. Possible values are:
|
4. After the request is verified, the API Gateway sends a response to the client. The following parameters are in the response body:
| Parameter | Description |
access_token |
The token that can be sent to the Resource Server to access the protected resources of the Resource Owner (user). |
refresh_token |
A token that may be used to obtain a new access token. |
expires |
The remaining lifetime on the access token. |
type |
Indicates the type of token returned. At this time, this field
always has a value of Bearer.
|
The following is an example response:
HTTP/1.1 200 OK
Cache-Control: no-store
Content-Type: application/json
Pragma: no-cache{
"access_token": “O91G451HZ0V83opz6udiSEjchPynd2Ss9......",
"token_type": "Bearer",
"expires_in": "3600",
}
5. After the Web server has obtained an access token, it can gain access to protected resources on the Resource Server by placing it in an
Authorization: Bearer HTTP header:
GET /oauth/protected HTTP/1.1
Authorization: Bearer O91G451HZ0V83opz6udiSEjchPynd2Ss9
Host: apigateway.com
For example, the
curl command to call a protected resource with
an access token is as follows:
curl -H "Authorization: Bearer O91G451HZ0V83opz6udiSEjchPynd2Ss9" https://apigateway.com/oauth
/protected
Note:
To run the sample(Sample Client,INSTALL_DIR/samples/scripts/oauth/authorization_code.py), perform the folllowing steps:
[oracle@cdcXXXX scripts]$ sh run.sh oauth/implicit_grant.py Go to the URL here: https://127.0.0.1:8089/api/oauth/authorize?cliend_id=SampleConfifentialApp& response_type=token&scope=https://localhost:8090/auth/userinfo.email&redirect _uri=https://localhost/oauth_callback&state=-1992846334
Enter Access Token code in dialog
********************ACCESS TOKEN RESPONSE8************************************ Access token received from authorization server a0b09580-1866-4dbc-a472-d89192 a9a95d ****************************************************************************** Now we can try access the protected resource using the access token Executing get request on the protected url Response from protected resource request is:500 Problem accessing the protected resource.Response code returned is:500
Root cause:
The authorization server encountered an unexpected condition that prevented it from fulfilling the request.(This error code is needed because a 500 Internal Server Error HTTP status code cannot be returned to the client via an HTTP redirect.)
For details, please refer to http://tools.ietf.org/html/rfc6749
4.1.2.1.Error Response
0 件のコメント :
コメントを投稿